Sniffing GSM traffic on a private cellphone network
Legal Disclaimer: GSM Research and Passive Traffic Monitoring
‘The information provided in this blog is for educational and informational purposes only. The author and publisher of this blog are not responsible for any misuse, illegal activities, or damages that may arise from the use of the information provided herein.
The author conducted research using two Samsung phones and a BladeRF with YateBTS to create a small-scale GSM network for the purpose of analyzing and intercepting traffic. It is important to note that intercepting or tampering with wireless communication without proper authorization is illegal in many jurisdictions. The author undertook this research within a controlled and lawful environment, and any techniques or findings described in this blog should not be replicated or applied in unauthorized or illegal activities.
The author strongly advises against engaging in any illegal activities, including but not limited to intercepting or tampering with wireless communications, without the express permission and authorization of the relevant authorities and stakeholders. Unauthorized interception of wireless communications violates privacy laws, regulations, and individual rights. Engaging in such activities may lead to severe legal consequences, including criminal charges and civil liabilities. It is always recommended to consult with legal professionals or authorized experts before conducting any research or experiments in the field of wireless communication.
The author disclaims any liability or responsibility for any damages, losses, or legal implications arising directly or indirectly from the use, misuse, or interpretation of the information provided in this blog.
By reading and using the information in this blog, you agree to the terms of this legal disclaimer and accept the risks associated with unauthorized interception or tampering with wireless communications.’
In this blog post I will be taking a look at cellular traffic and analyzing the GSM packets in Wireshark. However, I will also show how I have created a personal and portable, private cell phone network that I will use for this exercise. I created a portable cell phone network to ensure that I am operating and testing on frequencies that are not interfering or overlapping with any licensed operators in my area. I do not recommend that you attempt to follow along unless you understand how to properly do everything to stay within the bounds of your local laws, rules and regulations. It is illegal to interfere with licensed operators or to sniff the private traffic of individuals. To avoid these issues everything here is done in a private cell phone network I have created for this exercise with my own devices and cellular base station.
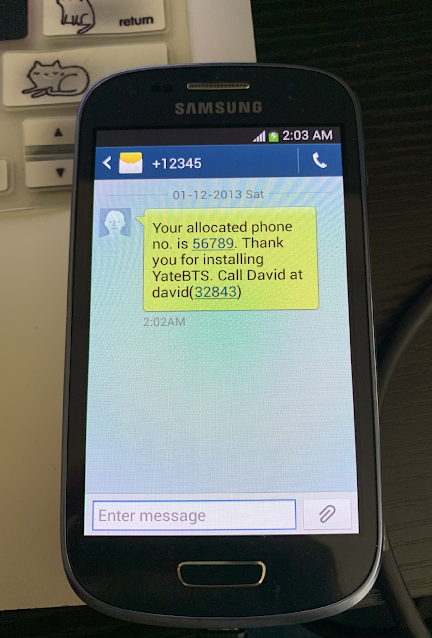
The interface for programming the IMSI on the SIM cards was interesting to work with. You also need to specify a KI value as well for authentication . This will come up again when we discuss the Kc value for decoding later on in another post. Here we are going to passively observe gsm network traffic on our own portable cellphone network. The SMS and voice decoding is beyond the scope of this post as for now we will be discussing how to set up a base station, have cellular devices join the private network. Then I will demonstrate how you can have the devices call and text one another on your private cellphone network. Additionally, on another machine I will show how the traffic can be observed and analyzed with a HackRF, grgsm_livemon and Wireshark. I programmed the two SIM cards with 15 digit IMSI numbers to be compatible with the Yate base station.
Here is what the SIM card reader/writer looks like in action. It's useful for setting up the devices with the YateBTS as I have read that although you can perhaps have your base station freely adopt new subscribers within certain IMSI ranges that at least with the BladeRF there seems to be better performance if the base station is programmed to add specific subscribers with IMSI numbers that are put directly into the backend interface. I did this to get ahead of any connectivity issues and found that the connectivity and service worked quite well and consistently.
After a little bit more configuration in regards to the frequencies being used the BTS will be ready to start. You need to be careful to not transmit at frequencies that can interfere with licensed operators in your area. I chose to create a 2G network on frequencies that definitely are not overlapping with other devices in my area. Additionally also at run time I use an RF enclosure to ensure that my transmissions are not unintentionally affecting anyone else in my area.
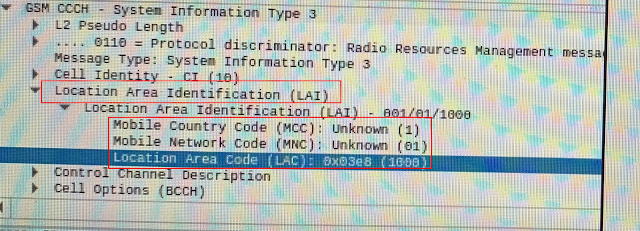
There are quite a few steps to get up and running but we have basically everything we need at this point. We created custom SIM cards to put on our devices, we have configured our local base station and loaded the appropriate FPGA bitstream to the BladeRF. Since I want to also see what is going on I will also at this point setup the observing machine with the HackRF. For this purpose I setup another laptop with DragonOS software. I initially scanned the area to see my base station and then since I created the base station I already had the exact transmission frequency that would normally need to be found at this step. Using a tool called grgsm_livemon I am able to monitor a single channel at a time. I additionally started up Wireshark to start monitoring for the GSMTAP packets to be able to later analyze them and learn about the test portable cell phone network I have setup.
And at this point we can definitely see the traffic flowing on our observation machine. As you can see below gr-gsm livemon is working well and is seeing everything from our base station and what is going on between our devices.















Comments
Post a Comment